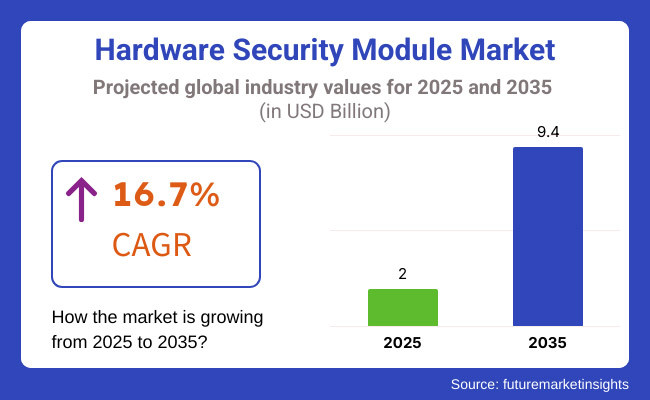
The hardware security market is expected to grow from USD 2.0 billion in 2025 to USD 9.4 billion by 2035, which means a compound annual growth rate (CAGR) of 16.7% for the predicted period. The outbreak of cyber threats, an increase in digital transactions, and the popularity of cloud-based security services are three main precipitating factors for this development. Following North America as a leader in cyber security investments, Europe strengthening its data protection regulations, and Asia Pacific quickly adopting digital transformation, the HSM market has every capability for substantial growth in the next decade.
Identified as a strong growth prospect, the hardware security module industry is expected to change significantly from 2025 to 2035 as more and more companies around the globe will utilize HSMs to keep sensitive information safe and comply with government regulations.
The year 2024 marked a number of the hardware security module market's significant breakthroughs, bringing about the transformation of the sector. IBM Corporation got a deal to replace HSMs with post-quantum cryptography PKI systems; thus, safeguarding data, the company ushered in the first move to fight off future quantum computing threats.
On the other hand, Thales TCT's termination of some HSM products has stressed the technical innovators' need to pursue security solutions, underlining the market's need for the steady creation of ideas. The launch of the KeyperPLUS network HSM, the most prominent HSM of Ultra Electronics, a next-generation solution aimed at boosting cryptographic security for critical infrastructure, has been another major advancement. The HSM innovations speak of a decisively evolving market reshaped by the digital world where the protection of confidential information becomes an explicit necessity.
Although the environment is generally seen as positive, hardware security modules still have to face some challenges, especially the high cost of implementation and complexity of integration. HSM solutions demand heavy initial investment in terms of hardware, software, and IT infrastructure; thus, they are quite difficult for SMEs to adopt. Those companies that are tactically on a path to capitalize on the promotion of flexible and easy-to-implement security solutions will definitely gain an edge over others as the market keeps changing.
The extensive cloud-to-HSM migration not only depicts a breakthrough in the development of cloud services in the future but also will increasingly help to secure the transparency of business operations. HSMs deployed in the cloud deliver the advantages of scale, remote manageability, and economic data loss protection, thereby making them a preferred choice for every organization.
Banks and Healthcare facilities are already utilizing these solutions for secure transactions, digital identity verification, and data encryption. Not only that, but the synergy of AI and Machine Learning with Cloud Cost HSM SaaS offerings also allows for predictive threat detection and provides real-time security monitoring, which strengthens their usage even further. As more and more companies go for the cloud, the demand for cloud HSMs is projected to boom, which, in turn, will create new markets and broader data security applications.
Explore FMI!
Book a free demo
The expansion of the Hardware Security Module (HSM) market is mainly attributed to the surge in data protection needs, a need for compliance with certain regulations, and a high level of modalities in encryption security across different sectors. HSM vendors are centered on making progress in the highly secure, scalable, and regulatory-compliant solutions that will satisfy the increasing requests from banks оn cloud service providers and firms. For financial institutions prioritizing encryption security, regulatory compliance, and performance, the preservation of sensitive financial transactions and personal data is a must.
High-performance HSMs that provide modular security for the cloud are service providers' priorities, fulfilling cloud apps with HSMs and thus flanking potential infiltrations in data. Cost-effective and secure solutions for securing digital assets sought by end users, inclusive of businesses and organizations, are not to be left out. The HSM market is definitely seeing an upward trend due to the increase in cyberattacks, the tightening of data protection regulations, and the emergence of more efficient cryptographic mechanisms. The combination of high technology with the exclusive service of cloud-based security and blockchain application connection is bringing dynamics to this market, making it one of the pillars of modern cybersecurity infrastructure.
Contract & Deals Analysis
| Company | Contract Value (USA USD Million) |
|---|---|
| IBM Corporation | Approximately USD 50 - USD 70 |
| Ultra Electronics | Approximately USD 20 - USD 30 |
From 2020 to 2024, the hardware security module (HSM) market expanded significantly with the rising need for secure encryption solutions, digital payment security, and adherence to strict data protection regulations. HSMs were adopted by financial services, healthcare, and government sectors to protect sensitive information, digital identities, and cryptographic keys. Scalability and accessibility became enhanced via HSMs in the cloud. Cybersecurity resilience was enhanced with AI's detection of threats.
Post-quantum cryptographic HSMs will evolve from 2025 to 2035, making use of post-quantum cryptography, blockchain-influenced security, and higher-level AI authentication schemes. HSMs will be instrumental for digital payments, IoT entities, and distributed identities. Security will be centered on edge security, zero-trust networks, and autonomous cryptography management systems, which defend against threats from increasing cyber-attacks and regulatory requirements.
A Comparative Market Shift Analysis 2020 to 2024 vs. 2025 to 2035
| 2020 to 2024 | 2025 to 2035 |
|---|---|
| HSMs enabled legacy encryption protocols such as RSA and ECC to secure digital identities and transactions. | Post-quantum cryptography (PQC) will go mainstream, providing quantum computing-protected resistance. AI-powered cryptographic engines will automatically respond to new security threats. |
| Cloud HSMs offered scalable key management solutions for multi-cloud and hybrid deployments. | Decentralized cloud HSMs, based on blockchain technology, will improve data integrity, transparency, and security on distributed networks. |
| Foundation quantum-resistant algorithms were brought in as a preventive measure. | Quantum-safe HSMs will also incorporate quantum key distribution (QKD) and quantum random number generators (QRNG) for unbreakable encryption. |
| AI-powered HSMs detect whether there is any suspicious activity, and therefore, threat intelligence is improved. | AI cognitive models will forecast cyber-attacks, take action on threats autonomously, and adaptively optimize crypto policies in real time. |
| Organizations implemented zero-trust models via identity-based authentication and access controls. | Fully autonomous zero-trust models based on AI and blockchain will provide continuous authentication, dynamic access control, and anticipatory threat defense. |
| HSMs protected IoT devices and edge computing nodes against data breaches and unauthorized access. | Quantum-secure edge HSMs will ensure end-to-end security for decentralized IoT networks, smart cities, and autonomous systems. |
| Compliance with GDPR, CCPA, and PCI-DSS spurred the adoption of HSMs in financial services and healthcare. | Compliance monitoring powered by AI will make audits easy and guarantee that the data is still secure. |
| HSMs protect digital identities, certificates, and payment transactions with multi-factor authentication (MFA). | Decentralized identity management using blockchain and quantum cryptography will allow self-sovereign identities and passwordless authentication. |
| HSMs interfaced with blockchain for secure digital signatures and smart contract execution. | Blockchain-born HSMs will enable decentralized finance (DeFi), digital asset custody, and cross-border digital identity authentication. |
| Financial services, healthcare, and government were the biggest users for regulatory compliance and data protection. | Telecom, energy, and smart cities will propel the demand for quantum-resistant HSMs to protect critical infrastructure and decentralized networks. |
Cyber threats are constantly evolving, which poses a significant risk to the hardware security module (HSM) market. Cybercriminals are becoming continually more specific and innovative with their attack methods, and HSM suppliers need to constantly build new security strategies to prevent vulnerabilities from being a risk. Since HSM is used to protect sensitive secrets, any security breaches in the HSM system could result in the loss of cryptographic keys, data leaks, and loss of reputation for the company.
Industry regulatory compliance is another primary concern, as banks, health care, and governmental entities are required to abide by some strict data security protocols. FIPS 140-2/3, PCI DSS, GDPR, and HIPAA require organizations to use cryptographic solutions that are secure without risk. In such events, non-compliance may lead to adverse consequences such as financial loss, penalties, and even risk of business shutdown.
Supply chain risks can affect the HSM production capabilities as well as its pricing strategies. The semiconductor shortages and the geopolitical tensions affecting the major manufacturing regions can result in the postponement of hardware production. The companies should take the steps necessary to develop resilient supply chains and modulate these risks through diverse sourcing strategies.
The exorbitant cost of HSM installation and upkeep is a constraint for the smaller companies. While the bigger businesses can manage the expense of encryption hardware, small and medium-sized enterprises (SMEs) encounter the challenge of the initial investment as well as the integration expenses, hampering their market capabilities.
Market rivalry is growing, with cloud-based HSM solutions taking the lead. The classical on-premise HSMs are indeed on the highest protection level, recyclers, but the cloud-based alternatives, instead of cost and size, offer a possibility of scaling. Companies that do not manage to adapt to new market needs will most likely partner with their customers to swift, adaptable competitors who are offering hybrid or cloud-native security solutions.
| Country | CAGR (%) |
|---|---|
| India | 17.9% |
| China | 17.8% |
| The USA | 17.5% |
| Australia | 16.6% |
| Germany | 16.5% |
| Japan | 16.4% |
America dominates the share for HSM, spearheaded mostly by stringent data protection regulations, cloud computing, and growing cyber-attacks. HSMs are extensively used by healthcare organizations, governments, and banks to safeguard data and support regulatory compliance. According to PCI DSS and FIPS, the payment and transaction business depends upon HSMs for safe electronic payment and transactions.
For companies in the healthcare industry, patient data is protected, and they are HIPAA-compliant through HSMs. HSMs are also used by cloud providers to protect encryption and cryptographic key management to allow secure data in the cloud.
FMI forecasts the USA market to grow at 17.5% CAGR over the research period.
Growth Drivers in the USA
| Key Drivers | Description |
|---|---|
| Tight Data Protection Regulations | HIPAA, PCI DSS, and FIPS compliance require advanced security products like HSMs. |
| High Cybersecurity Awareness | Increasing cyber-attacks and data breaches compel organizations to utilize HSMs for improved security. |
| Cloud Computing Growth | HSMs contribute significantly towards secure key management and encryption within cloud offerings. |
China's HSM market is seeing fast growth driven by accelerating digitalization, rigorous cybersecurity requirements, and growing online payment and e-commerce usage. Banks use HSMs in some payment transaction processing and transaction encryption, especially with the ELV digital wallets they provide as online banking continues to grow.
Compliance with cybersecurity law forces companies to implement high-grade data protection, which in turn forces them to implement HSMs for encryption and authentication. Additionally, the prevalent use of cloud computing and IoT technologies triggers the need for HSMs to store and share data securely.
Growth Drivers in China
| Key Drivers | Description |
|---|---|
| Cybersecurity Regulations | The Cybersecurity Law requires strong data protection, forcing HSM uptake. |
| Digital Payment Security | Mobile payment and e-commerce growth calls for reliable cryptography solutions. |
| Cloud and IoT Development | HSMs provide robust authentication and data protection for cloud computing and IoT environments. |
The HSM market in Germany prospers due to stringent data privacy regulations, significantly developed industrial platforms, and Industry 4.0 use of technologies. Organizations use HSMs to have secure data encryption, key handling for crypto, and digital signatures for GDPR compliance.
The banking industry depends upon HSM for security in e-banking and e-payment, and business enterprises engaged in industrial manufacturing business use HSM in Industrial Internet of Things (IIoT) applications for end-to-end secure communication and integrity of data. The high sense of urgency towards security, even when there is cybersecurity, is turning German business enterprises into a high-end demand generator for high-level HSM solutions.
Market analysis by FMI indicates the growth in the German market would be at 16.5% CAGR in the forecast period.
Growth Drivers in Germany
| Key Drivers | Description |
|---|---|
| GDPR Compliance | Stringent rules necessitate strong security solutions such as the use of HSMs. |
| Industrial IoT Security | Industrial-oriented IIoT platforms leverage HSMs to provide safe communication and data integrity. |
| Digital Banking Security | Banks employ HSMs for safe online banking and anti-fraud security. |
The Australian HSM market continues to grow steadily due to the strength of data privacy regulation, heightened cybersecurity awareness, and faster digitization of banking operations. HSMs are utilized in companies to facilitate encrypted security, digital signatures, and authentication for Privacy Act and Consumer Data Right (CDR) compliance mandates.
Growth Drivers in Australia
| Key Drivers | Facts |
|---|---|
| Severe Data Privacy Regulations | Demand for HSMs is fueled by the Privacy Act and adhering to CDR. |
| Digital Banking Protection | HSMs are utilized by banks to facilitate secure online banking and prevention against fraud. |
| Initiatives of National Cybersecurity | Efforts from the government towards more cyber awareness propel HSM adoption. |
LAN or Network attached HSMs are gradually becoming the carrier of the largest environment in the whole hardware security module market due to their scalable growth, competitive computation power, and centralized management functions. HSMs are designed for large-scale enterprises and cloud service providers as they provide secure storage and management of cryptographic keys over a network. A major contributing factor to their widespread adoption is their capability to support numerous applications and users simultaneously without sacrificing security or performance.
With organizations looking at digital transformation and moving towards cloud-based environments, there is increasing demand for hot HSMs that are attached to the network in essentially a Celestial setup.
Furthermore, network-attached HSMs are essential for compliance and regulatory requirements such as PCI DSS, FIPS 140-2 and GDPR. Said systems provide tamper-proof key storage and auditable security operations that help organizations auto-comply with the highest data security norms and disorders. Multi-tenancy support for network-attached HSMs is also emerging as a common deployment method (particularly for Managed Security Service Providers (MSSPs) looking to provide HSM-as-a-Service solutions to multiple clients without compromising security.
Embedded or plugin Hardware Security Modules (HSMs) are dedicated security appliances that are primarily used within a hardware stack to perform cryptographic functions and securely manage cryptographic keys. In addition, integrating them into already established hardware is less complex and saves us from having to purchase separate external devices.
The IoT space has an embedded plugin HSM called iShield HSM by Swissbit that can be seamlessly integrated as an HSM. This plug-and-play USB security anchor enables system integrators to upgrade deployed AWS IoT Greengrass eligible devices with strong hardware security to protect their private keys and certificates from being revealed or duplicated in software.
With global transactions trending as increasingly cashless and more towards electronic methods, payment processing is a major driver fueling growth in the Hardware Security Module (HSM) market. With secure PIN management, transaction encryption, and cryptographic key management, HSMs help safeguard confidential payment information to maintain its security and authenticity. For this reason, HSMs are commonly utilized by financial institutions, payment processors, and fintech companies to mitigate fraud, safeguard online transactions, and adhere to requirements such as the Payment Card Industry Data Security Standard (PCI DSS).
As an example, Entrust provides the nShield HSMs that ensure certified protection of private code signing keys and support the secure execution of digital signature processes. Likewise, Aujas offers an automated code-signing solution for DevOps, named CodeSign, which works well with HSMs, enabling management and scalability of the code-signing processes while ensuring software authenticity and compliance with rigorous security standards.
The hardware security module market is quite hyped now, considering that the entire world is turning towards the security of data instead of just compliance with regulatory mandates and adopting the use of the cloud. An HSM is a major component in the security of a cryptographic key, as well as encryption and strong authentication from enterprises and governmental institutions.
Industrial leaders such as Thales Group, Entrust, Utimaco, IBM, and Futurex dominate the industry by providing superior-performing HSMs integrated with cloud and post-quantum cryptography support alongside value-added key management capabilities. Thales as well as IBM strengthen positions through strategic acquisitions while offering cloud-based HSM services. In contrast, Utimaco and Futurex focus on customizable, regulatory-compliant solutions for financial services and IoT security.
Emerging players and niche firms are spearheading the trend towards very lightweight, highly scalable, and cost-effective HSMs for edge computing, blockchain applications, and fintech services. As the threat landscape continues to evolve, parameters such as acquiring FIPS-certified, AI-driven threat detection, and quantum-resistant encryption solutions will garner a considerable lead for companies in this growing security landscape.
Market Share Analysis by Company
| Company Name | Estimated Market Share (%) |
|---|---|
| Thales Group (Gemalto) | 18-23% |
| Utimaco GmbH | 15-20% |
| Futurex | 10-15% |
| Yubico | 8-12% |
| IBM Corporation | 7-11% |
| Other Companies (combined) | 30-42% |
Key Company Offerings and Activities
| Company Name | Key Offerings/Activities |
|---|---|
| Thales Group (Gemalto) | Provides cloud-integrated HSMs with advanced cryptographic key management and compliance solutions. Focuses on scalable, multi-cloud security. |
| Utimaco GmbH | Specializes in modular HSM solutions for enterprise security and compliance. Expand into IoT and cloud security with AI-driven encryption. |
| Futurex | Offers high-performance HSMs for payment security and data encryption. Focuses on cloud-based key management and tokenization solutions. |
| Yubico | Develops hardware authentication keys and HSMs for identity and access management. Emphasizes multi-factor authentication and zero-trust security. |
| IBM Corporation | Integrates HSMs with cloud security and quantum-safe cryptography. It focuses on secure data processing and compliance with hybrid cloud environments. |
Thales Group (Gemalto) (18-23%)
Thales is the market leader in hardware security modules, leveraging its expertise in cryptographic key management and compliance. The company focuses on cloud integration, providing scalable HSM solutions compatible with multi-cloud environments. Thales continues to enhance its HSMs with quantum-safe encryption, ensuring data security against future cyber threats. Its strategic direction includes expanding partnerships with cloud service providers and investing in AI-driven cryptographic solutions.
Utimaco GmbH (15-20%)
Utimaco is known for its modular HSM solutions catering to enterprise security and regulatory compliance. The company is expanding its product portfolio into IoT and cloud security, leveraging AI-driven encryption and identity management. Utimaco focuses on delivering flexible, scalable HSMs for diverse industries, including financial services, healthcare, and government. Its strategic direction includes enhancing key management automation and collaborating with cybersecurity firms for integrated solutions.
Futurex (10-15%)
Futurex specializes in high-performance HSMs for payment security and data encryption. The company focuses on cloud-based key management, tokenization, and data protection solutions for financial institutions and enterprises. Futurex is investing in next-generation encryption algorithms and AI-based security analytics to enhance threat detection and data integrity. Its strategic outlook includes expanding its global reach through partnerships with payment processors and cloud service providers.
Yubico (8-12%)
Yubico is a leading provider of hardware authentication keys and HSMs for identity and access management. The company emphasizes multi-factor authentication, zero-trust security, and compliance with industry standards. Yubico is enhancing its hardware security devices with biometric authentication and passwordless login solutions. Its strategic focus includes expanding its product ecosystem to support hybrid and multi-cloud security architectures.
IBM Corporation (7-11%)
IBM integrates its HSMs with cloud security and quantum-safe cryptography, focusing on secure data processing and regulatory compliance. The company is investing in advanced cryptographic technologies, including lattice-based encryption, to safeguard sensitive data against quantum computing threats. IBM’s strategic direction includes enhancing its hybrid cloud security platform with AI-driven threat intelligence and expanding its partnerships for secure digital transformation.
Other Key Players (30-42% Combined)
The global Hardware Security Module (HSM) industry is projected to witness a CAGR of 16.7% between 2025 and 2035.
The global Hardware Security Module (HSM) industry stood at USD 2.0 billion in 2025.
The global Hardware Security Module (HSM) industry is anticipated to reach USD 9.4 billion by 2035 end.
North America is expected to record the highest CAGR, driven by increasing data security regulations and the adoption of cloud-based HSMs.
The leading companies in the industry include Thales Group (Gemalto), Utimaco GmbH, Futurex, Adweb Technologies, Yubico, Atos, Ultra Electronics, SPYRUS, Inc., Securosys, Entrust Corporation, Nitrokey, Kryptoagile, and IBM Corporation.
Remote Construction Market Analysis by Component, Application, End-use Industry and Region Through 2035
Procurement as a Service Market Trends – Growth & Forecast 2025 to 2035
Massive Open Online Course Market Analysis – Growth, Trends & Forecast 2025 to 2035
Tactical Radios Market Analysis by Type, Application, and Region Through 2025 to 2035
Healthcare Virtual Assistants Market Analysis by Product, End User and Region Through 2035
Microsoft Dynamics Market Trends - Demand & Forecast 2025 to 2035
Thank you!
You will receive an email from our Business Development Manager. Please be sure to check your SPAM/JUNK folder too.