The 5G Security Market is estimated to be valued at USD 2.4 billion in 2025 and is projected to reach USD 25.2 billion by 2035, registering a compound annual growth rate (CAGR) of 26.4% over the forecast period.
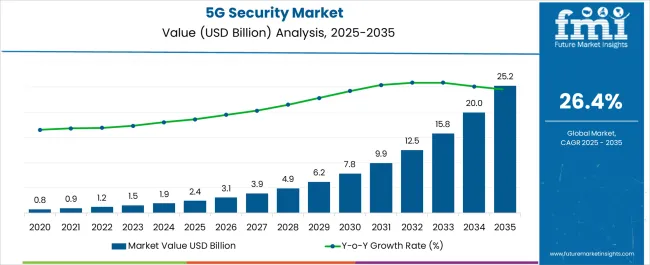
| Metric | Value |
|---|---|
| 5G Security Market Estimated Value in (2025 E) | USD 2.4 billion |
| 5G Security Market Forecast Value in (2035 F) | USD 25.2 billion |
| Forecast CAGR (2025 to 2035) | 26.4% |
The 5G security market is experiencing significant momentum as telecom operators, enterprises, and governments increasingly prioritize network protection amid rapid 5G rollout. The expansive data throughput and ultra-low latency of 5G are enabling mission-critical applications, making robust cybersecurity frameworks a strategic imperative.
With the rise of edge computing, IoT ecosystems, and software-defined networks, the threat landscape has widened, necessitating end-to-end security models. National security regulations, zero-trust architecture adoption, and heightened consumer privacy expectations are driving investments in both hardware- and software-based solutions.
Furthermore, the deployment of standalone 5G architecture is creating new attack surfaces, prompting vendors to innovate across core and edge security layers. Strategic alliances between telecom providers and cybersecurity firms are further accelerating market maturity. The future of this market lies in AI-driven threat detection, cloud-native security models, and proactive network orchestration to defend against evolving vulnerabilities.
The market is segmented by Component, Network Component Security, Architecture, End User, Deployment Type, and Vertical and region. By Component, the market is divided into Solutions and Services. In terms of Network Component Security, the market is classified into Core Security and RAN Security. Based on Architecture, the market is segmented into 5G NR Standalone and 5G NR Non-standalone. By End User, the market is divided into Telecom Operators and Enterprises. By Deployment Type, the market is segmented into Cloud and On-Premises. By Vertical, the market is segmented into Manufacturing, Healthcare, Energy and Utilities, Retail, Automotive and Transportation, Public Safety, Media and Entertainment, and Others. Regionally, the market is classified into North America, Latin America, Western Europe, Eastern Europe, Balkan & Baltic Countries, Russia & Belarus, Central Asia, East Asia, South Asia & Pacific, and the Middle East & Africa.
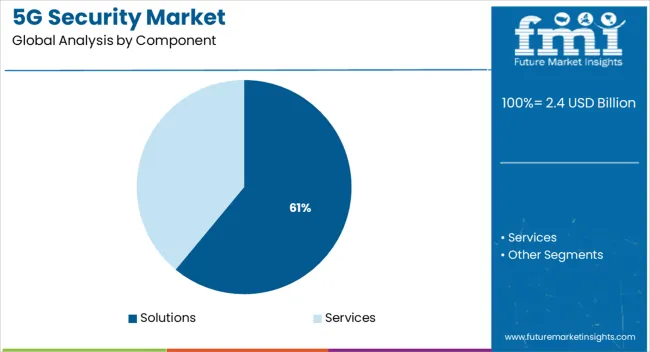
Solutions are expected to account for 61.0% of the total revenue share in the 5G security market by 2025, making them the leading component segment. This dominance is being driven by the demand for scalable and software-defined tools capable of addressing dynamic security threats in real time.
Network operators are investing in intrusion detection systems, firewalls, threat intelligence, and secure network slicing solutions to safeguard increasingly virtualized environments. The ability to deliver layered, policy-driven protection across 5G RAN, transport, and core layers has made solutions the cornerstone of most security deployments.
Additionally, the growing preference for SaaS-based security platforms has improved accessibility and manageability, particularly for multi-cloud 5G infrastructure. As enterprises seek unified visibility and real-time response capabilities, security solutions are expected to remain the foundation of 5G threat management strategies.
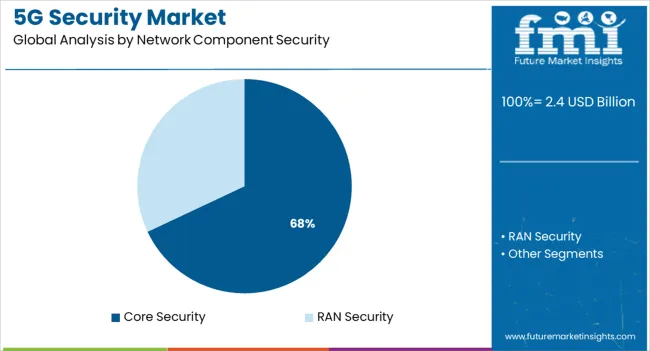
Core security is projected to hold 68.0% of the total share in the 5G security market by 2025, making it the dominant network component subcategory. This lead is being driven by the critical role of the 5G core in managing subscriber authentication, session control, and data routing—all of which are prime targets for cyberattacks.
The shift from hardware-centric to virtualized and cloud-native cores has necessitated a rethink of traditional perimeter defenses. Enhanced encryption, network slicing security, and user plane integrity mechanisms are being deployed to secure the 5G core from emerging threats.
Regulatory mandates on data sovereignty and integrity are also placing pressure on operators to reinforce their core security posture. With increased reliance on cloud-based infrastructure, the core is expected to remain the focal point for advanced 5G cybersecurity frameworks.
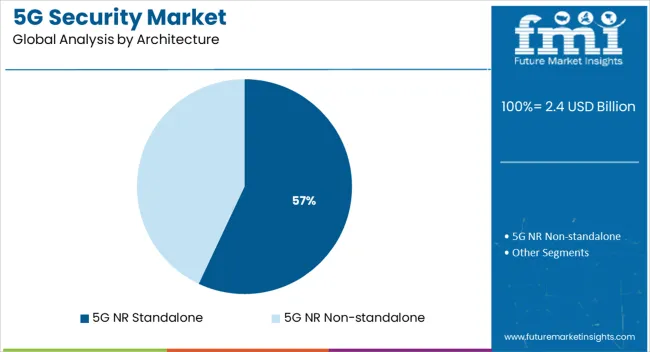
5G NR standalone (SA) architecture is anticipated to contribute 57.0% of the total market revenue by 2025, positioning it as the leading architectural model from a security perspective. This growth is attributed to the full decoupling from 4G LTE infrastructure, which introduces a completely new network core with advanced capabilities and corresponding vulnerabilities.
Unlike non-standalone deployments, SA architecture requires a comprehensive approach to securing cloud-native components, service-based architecture interfaces, and edge compute nodes. Enhanced mobile broadband, ultra-reliable low-latency communication, and massive machine-type communication all demand robust security orchestration at every layer.
The adoption of SA by governments and enterprise networks for critical applications has accelerated investment in dedicated SA security solutions. As more operators transition to full SA deployment to unlock 5G's true potential, its associated security landscape will continue to evolve and expand.
Several factors, including network slicing and significant security augmentation over 4G and LTE, are driving the demand for 5G security. When data is encrypted, 5th-generation technology prioritizes the privacy of both companies and people. As a result, hackers find it more challenging to decode the data. Additionally, the data is available quickly since it is routed via virtual switches and hubs rather than any other hardware component.
Fifth-generation technology is being used, it is anticipated that this would draw clients, corporate users, and mobile phone network carriers to a single platform. This will create a dependency between company activities that are digitally and automatically controlled and operated, as well as the management and use of corporate machinery. Additionally, the telecom systems' cyber-physical interdependence will be strengthened, and other infrastructural providers' smart connections will help to provide creative mobile network access. Such benefits are expected to boost the global demand for the 5G security market.
Numerous operators have concentrated on safeguarding their carrier network in light of the surge in network attacks. In the aftermath of the bank theft, for instance, O2 Telefonica in Spain hired 1,100 security personnel and 660 analysts to work in 7 Security Operations Centers (SOCs) all throughout the globe. Additionally, 3,100 security professionals are employed by British Telecom (BT), which has 15 security operations centers across the world and is licensed by the UK government to verify its network systems.
BT discusses utilizing artificial intelligence (AI) to protect the data of its customers. Its robot-assisted cyber threat scanning technology locates and comprehends cybersecurity vulnerabilities across huge datasets using visual representations. The cost of network security measures will significantly increase as a result of these costs.
Depending on component type, the 5G security market is divided into services and solutions. During the anticipated period, the market for services is anticipated to increase profitably. A complete, unconventional, adaptable, and expandable end-to-end system is demonstrated by 5G.
Customers who use 5G services can access apps that support the Internet of Things (IoT), extremely real-time communications (RTC), ultra-reliable communication systems, and broadcast-like applications.
Fifth-generation services meet the growing consumer desire for mobile on-the-go services integrated into cars that offer in-vehicle services and assistance during vehicle inspections and automated driving applications. Also, solutions aimed at certain business verticals including financial services, healthcare, automotive, media, and others have fifth-generation security enabled across a variety of industry verticals. The flexibility of the 5G security services allows for the creation of creative partnerships and adaptable business models.
Companies always have imminent threats regarding data breaches, data theft, and cyber-attack. To prevent the attacks companies are implementing 5G security architecture into their systems. This attack can be caused because of malevolent organizations associated with networks by unidentified network devices, and poor information encryption can cause a breach of sensitive information. As more companies are interested in converting their conventional work form into fully automated and digital platforms, there is always a threat of cyber-attack.
5G technology enhances security by providing advanced features like user authentication, enhanced user privacy, and strong network authorization. With 5G security, businesses are able to encrypt information, safeguard its integrity, and perform verification during the information transmission process. Numerous industries are worried about the security of their IoT gadgets as they contain data like individual information, business-sensitive data, and basic framework.
As the 5G penetration is projected to skyrocket in the coming years, there are high speculations of their security breach. Businesses around the globe thus have become agile towards the implementation of 5G security into their operations. This is consequently expected to drive the 5G security market at a significant pace in the coming decade.
With the growing concern of consumers worldwide regarding their health and their growing annual healthcare budget, healthcare stakeholders are becoming richer every day. But, at the same time, the evolution of new technologies and their need for speed and automation have made them vulnerable to cyber threats. 5G capabilities have added numerous advantages to the healthcare sector including speed, capacity, hyper-connectivity, low latency, and data-driven insights. The higher speed and lower latency offered by 5G can be a boon to cyber attackers as it offers the opportunity to access more data due to hyper-connectivity.
Besides, the connectivity of multiple healthcare devices and processes further makes the entire system vulnerable if attacked once. The other types of 5G security threats can be in terms of DoS and DDoS attacks and jamming of networks. These security threats have made healthcare fraternities ponder prospective solutions, such as 5G security. Healthcare IT expenditure stands at nearly USD 74 Billion and is growing at an annual rate of over 10%. 5G Security being a part of and of utmost importance to healthcare providers, is expected to garner a fair share of this expenditure in the coming decade.
The Telecom industry is responsible for the transfer of voice and data across the globe with high consistency and quality. Users can stay connected across the globe without any interruption with the help of better technology. Increasing use of mobile networks to access video content, digital payments, online retail, and video conferences have contributed to mobile traffic. During a pandemic, mobile traffic has surged nearly 60% globally. Subscriber data contains communication information as well as subscriber-related data, for example, identities, geographical location, membership profiles, and call data records. Operators are bending towards the 5G technology to protect the subscriber’s information and ensure the threats regarding data breaches.
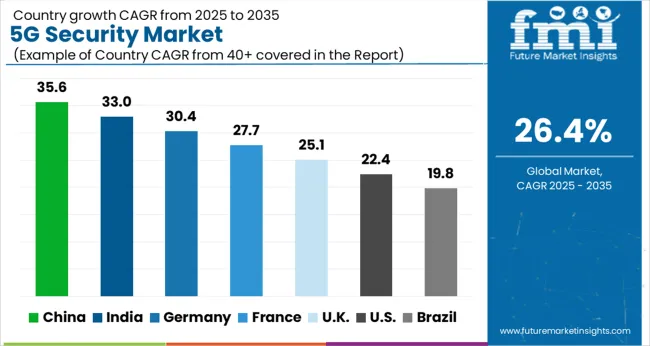
The USA is considered a lucrative market for 5G Security and is expected to register a significant CAGR of 25.9% for the forecast period 2025 to 2035. This 5G security strategy offers a far more effective way to deal with network advancements, expanding the technology strength of the USA to develop and contribute while planning government strategies to help and supplement those qualities.
The 5G security market in China is expected to register a CAGR of 25.6% during the forecast period. China has currently 1.43 million 5G base stations and over 500 million 5G subscribers. Based on the number of subscribers, the implementation of 5G security to ensure data safety is done lucratively. China will work with different partners to promote advancing 5G applications in many industries that target data security. China is expected to accomplish a few steps forward in 5G security advancement as it is prone to most cyber-attacks.
North America is holding a significant share of the 5G security market. North America has significant developments in 5G technology, and certain security measures are taken to eliminate the leak. North America is doing a prominent job distributing spectrum for 5G, both high-band and low-band. On the other hand, it lags behind in the distribution of the mid-band spectrum. If North America is to remain competitive in the new digital world, it must repurpose the mid-band spectrum for 5G. Some incumbent spectrum holders may object to repurposing, although the national security constraints that determine spectrum allocations have evolved. North America is competing in a world where technical and economic leadership are just as vital as military might, because of which implementation of 5G security is growing prominently.
The solutions segment is having the largest market share in the forecast period. It is expected to grow at a CAGR of 25.8% in the next ten years. Solutions comprise all the necessary tools responsible to ensure safety. Some tools are next-generation firewalls, data loss prevention, antivirus/antimalware, DDoS protection, security gateway, and sandboxing which are used to ensure 5G security.
Next-generation firewalls are an effective method that provides a series of layers before entering into the main frame. Companies using next-generation firewalls are Avangrid, Flexential, Avantor Inc., Worldpac, and PAE to ensure strong 5G security.
Data Loss Prevention gives command over who might access as well as share their information. DLP instruments help to plan Data Loss Prevention methodologies by giving pre-characterized approach controls to follow the development of information. It additionally forestalls unapproved sharing, moving, as well as leaks of information. According to Verizon’s 2024 Data Breach Investigations Report, the malware was involved in nearly 15% of data breaches. The average time taken to identify and contain data breach is around 287 days. Due to this various industries are implementing security solutions to maintain security.
5G non-standalone architecture is expected to grow at a CAGR of 24.9% for the forecast period of 2025 to 2035. The first rollout of 5G networks is a Non-standalone arrangement that draws attention toward enhanced broadband to give higher information transmission capacity and reliable connectivity. They are in accordance with the 3GPP determination that early rollouts of 5G network and gadgets be brought under NSA activity - meaning, the 5G network will be helped by the existing 4G framework. Therefore, specialist organizations that need to be the first to offer 5G speeds will begin with NSA and, when 5G inclusion is laid out, carry out independent 5G. Due to the above reason the cost for 5G non-standalone is less than 5G standalone. Companies are keen to invest in 5G security which has implemented 5G non-standalone architecture because of the cost-effectiveness.
5G networks, which are cloud supportive, will be a worthwhile objective for cyber threat bodies who are interested in corrupting, stealing, and compromising the data. To counter this, 5G cloud infrastructure is configured to restrict unauthorized access to secure network functions.
Companies have been successfully implementing the cloud infrastructure, with the help of artificial intelligence and machine learning companies are automating the process and the data or formula details are stored in the cloud platform which can be accessed remotely. Besides, Implement Secure Identity and Access Management (IDAM) is prominently used in the 5G cloud.
In North America companies implementing the 5G cloud mushroomed by 78% in the pandemic era, owing to a nearly 600% increase in cyber-attacks in the pandemic period compared to the previous years.
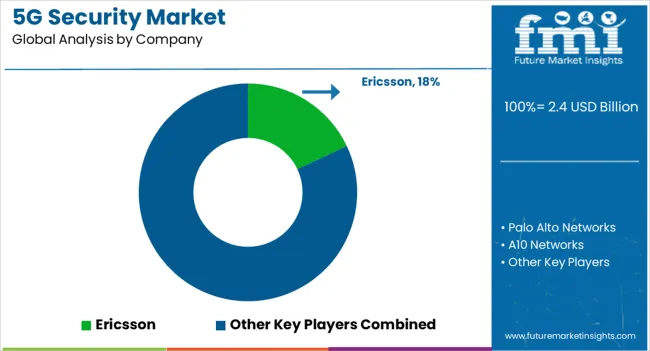
Leading players operating globally in the market are focusing on expansion, development, and new product launches in order to expand their business globally.
| Attribute | Details |
|---|---|
| Forecast Period | 2025 to 2035 |
| Historical Data Available for | 2020 to 2024 |
| Market Analysis | USD Million for Value |
| Key Regions Covered | North America; Latin America; Europe; Asia Pacific & MEA |
| Key Countries Covered | United States of America, Canada, Brazil, Mexico, Germany, Italy, France, UK, Russia, BENELUX, China, Japan, South Korea, GCC Countries, South Africa, Turkey |
| Key Segments Covered | Component, Network Component Security, Architecture, End User, Deployment Type, Vertical, and Region. |
| Key Companies Profiled | Ericsson; Palo Alto Networks; A10 Networks; Allot; Huawei; Nokia; Juniper Networks; Fortinet; Mobileum; ZTE |
| Report Coverage | Market Forecast, Company Share Analysis, Competition Intelligence, Drivers, Restraints, Opportunities and Threats Analysis, Market Dynamics and Challenges, and Strategic Growth Initiatives |
| Customization & Pricing | Available upon Request |
The global 5G security market is estimated to be valued at USD 2.4 billion in 2025.
The market size for the 5G security market is projected to reach USD 25.2 billion by 2035.
The 5G security market is expected to grow at a 26.4% CAGR between 2025 and 2035.
The key product types in 5G security market are solutions, _next-generation firewall, _data loss prevention, _antivirus/antimalware, _ddos protection, _security gateway, _sandboxing, _others, services, _consulting services, _implementation services and _support and maintenance services.
In terms of network component security, core security segment to command 68.0% share in the 5G security market in 2025.
Our Research Products

The "Full Research Suite" delivers actionable market intel, deep dives on markets or technologies, so clients act faster, cut risk, and unlock growth.
The Leaderboard benchmarks and ranks top vendors, classifying them as Established Leaders, Leading Challengers, or Disruptors & Challengers.

Locates where complements amplify value and substitutes erode it, forecasting net impact by horizon

We deliver granular, decision-grade intel: market sizing, 5-year forecasts, pricing, adoption, usage, revenue, and operational KPIs—plus competitor tracking, regulation, and value chains—across 60 countries broadly.

Spot the shifts before they hit your P&L. We track inflection points, adoption curves, pricing moves, and ecosystem plays to show where demand is heading, why it is changing, and what to do next across high-growth markets and disruptive tech

Real-time reads of user behavior. We track shifting priorities, perceptions of today’s and next-gen services, and provider experience, then pace how fast tech moves from trial to adoption, blending buyer, consumer, and channel inputs with social signals (#WhySwitch, #UX).
Partner with our analyst team to build a custom report designed around your business priorities. From analysing market trends to assessing competitors or crafting bespoke datasets, we tailor insights to your needs.
Supplier Intelligence
Discovery & Profiling
Capacity & Footprint
Performance & Risk
Compliance & Governance
Commercial Readiness
Who Supplies Whom
Scorecards & Shortlists
Playbooks & Docs
Category Intelligence
Definition & Scope
Demand & Use Cases
Cost Drivers
Market Structure
Supply Chain Map
Trade & Policy
Operating Norms
Deliverables
Buyer Intelligence
Account Basics
Spend & Scope
Procurement Model
Vendor Requirements
Terms & Policies
Entry Strategy
Pain Points & Triggers
Outputs
Pricing Analysis
Benchmarks
Trends
Should-Cost
Indexation
Landed Cost
Commercial Terms
Deliverables
Brand Analysis
Positioning & Value Prop
Share & Presence
Customer Evidence
Go-to-Market
Digital & Reputation
Compliance & Trust
KPIs & Gaps
Outputs
Full Research Suite comprises of:
Market outlook & trends analysis
Interviews & case studies
Strategic recommendations
Vendor profiles & capabilities analysis
5-year forecasts
8 regions and 60+ country-level data splits
Market segment data splits
12 months of continuous data updates
DELIVERED AS:
PDF EXCEL ONLINE
5G Electromechanical RF Switch Market Size and Share Forecast Outlook 2025 to 2035
Security Tape Market Size and Share Forecast Outlook 2025 to 2035
5G Solid State Switches Market Size and Share Forecast Outlook 2025 to 2035
5G Gain Block Amplifier Market Size and Share Forecast Outlook 2025 to 2035
5G Driver Amplifier Market Size and Share Forecast Outlook 2025 to 2035
Security Alarm Communicator Market Size and Share Forecast Outlook 2025 to 2035
Security and Vulnerability Management Market Forecast and Outlook 2025 to 2035
5G Millimeter Wave RF Transceiver Market Size and Share Forecast Outlook 2025 to 2035
Security Holograms Market Size and Share Forecast Outlook 2025 to 2035
Security Paper Market Size and Share Forecast Outlook 2025 to 2035
5G Testing Market Size and Share Forecast Outlook 2025 to 2035
5G in Healthcare Market Analysis Size and Share Forecast Outlook 2025 to 2035
Security System Tester Market Size and Share Forecast Outlook 2025 to 2035
Security Advisory Services Market Size and Share Forecast Outlook 2025 to 2035
5G Temperature-Compensated Crystal Oscillator (TCXO) Market Size and Share Forecast Outlook 2025 to 2035
Security Room Control Market Size and Share Forecast Outlook 2025 to 2035
5G Remote Surgery System Market Analysis - Size, Share, and Forecast Outlook 2025 to 2035
5G Telemedicine Platform Market Size and Share Forecast Outlook 2025 to 2035
Security Cameras (IR Illuminator) Market Size and Share Forecast Outlook 2025 to 2035
5G Industrial IOT Market Size and Share Forecast Outlook 2025 to 2035
Thank you!
You will receive an email from our Business Development Manager. Please be sure to check your SPAM/JUNK folder too.
Chat With
MaRIA